|
Voiced by Amazon Polly |
Introduction
Due to security concerns, sometimes third-party applications or web services are restricted to access through the public internet. To get access in such cases, you have to be in their network only.
Establishing a site-to-site VPN between two parties can help gain access to their network. In this blog, we will go through how to set up a site-to-site VPN connection between AWS ec2 instances and third-party OpenSwan firewall ( OpenSwan is a “software VPN” which runs on a Linux-based EC2 instance). We must create a VPN tunnel between AWS VPC and OpenSwan firewall to achieve this.
Customized Cloud Solutions to Drive your Business Success
- Cloud Migration
- Devops
- AIML & IoT
Prerequisites
- AWS Account
Step to Configure S2S VPN
- Log in to your AWS Account and go to the EC2 service
- Launch the instance in a public subnet in N. Virginia region will configure the OpenSwan firewall on top of it and act as a customer side.
3. Configure the security group and allow TCP, ICMP, and UPD traffic from VPC in the Mumbai region and SSH from your machine public IP.

4. Now launch an EC2 instance in a private subnet in Mumbai region as AWS side.
5. Allow all TCP, SSH, and ICMP traffic on the above created ec2 instance from the firewall side network configured above steps N. Virginia region.

6. Afterward, go to Virtual Private Gateway in Mumbai region and click on create “virtual private gateway” with named “s2s-vgw” and Amazon default ASN.

7. Now attach the newly created “s2s-vgw” with your VPC in Mumbai region.

8. Once attached, go to the “Site-to-Site VPN connections” service and click “Create VPN connection”.

9. Now fill in the below details under the “Create VPN connection” page and keep others default
- Name tag: s2s-customer-vpn
- Target gateway type: Virtual private gateway created above
- Customer Gateway: New
- IP address: Public IP of OpenSwan firewall created in N. Virginia
4. Routing option: Static (supported by OpenSwan)
5. Static IP prefixes: firewall side CIDR (20.0.0/16)


10. Now download the VPN configuration file by selecting the newly created VPN connection, and after that, click on “Download configuration.”
- Vendor: OpenSwan
- Platform: OpenSwan
- Software: OpenSwan 2.6.38+
- Ikev: ikev1

11. Now SSH into the OpenSwan instance created in the N. Virgina region and follow the steps to configure the customer side’s OpenSwan firewall and VPN configuration.
12. To install OpenSwan execute the command “yum install openswan –y”
13. After that, follow the instructions in the above downloaded configuration file and configure Tunnel 1 steps.
Note:
- Disable Source/destination check for OpenSwan instance

- Enable route propagation for the Private route table in the Mumbai region.

- In the configuration file, left subnet is the customer side, i.e., in N. Virginia region and right subnet in VPC CIDR in Mumbai region

Testing
14. Static routing supports route-based VPN, so only Tunnel 1 will go up

15. Now to test the connection, ping the AWS instance in the private subnet of the Mumbai region from the Openswan firewall instance to test the connection and ping from AWS to Openswan Firewall private IP to test the connection.
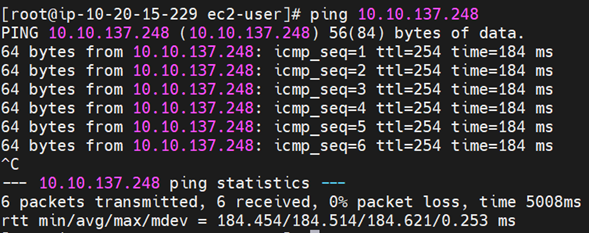
Conclusion
If you can ping, you successfully created a site-to-site VPN between AWS and Openswan.
If you get any errors, check the Security Group rules, Route Tables, and VPN configuration again. Then you can cross check the configuration matches with the other side.
Get your new hires billable within 1-60 days. Experience our Capability Development Framework today.
- Cloud Training
- Customized Training
- Experiential Learning
About CloudThat
CloudThat is also the official AWS (Amazon Web Services) Advanced Consulting Partner and Training partner and Microsoft gold partner, helping people develop knowledge of the cloud and help their businesses aim for higher goals using best in industry cloud computing practices and expertise. We are on a mission to build a robust cloud computing ecosystem by disseminating knowledge on technological intricacies within the cloud space. Our blogs, webinars, case studies, and white papers enable all the stakeholders in the cloud computing sphere.
Drop a query if you have any questions regarding Amazon VPC, OpenSwan Firewall and I will get back to you quickly.
To get started, go through our Consultancy page and Managed Services Package that is CloudThat’s offerings.
FAQs
1. How does an AWS Site-to-Site (S2S) VPN connection work with VPC?
ANS: – An AWS S2S VPN connection connects your VPC to your on-premise network. Amazon supports IPsec VPN connections. Data transferred between your VPC and on-premise routes over an encrypted VPN connection to help provide the confidentiality and integrity for data transfer. An Internet gateway is not needed to setup a Site-to-Site VPN connection.
2. What is the approx. maximum throughput of a S2S VPN connection?
ANS: – Every AWS S2S VPN connection network has two tunnels, each with a max throughput of up to 1.25 Gbps. If the VPN connection is to a Virtual Private Gateway (VGW), aggregated throughput limits would apply to your connection.
3. What factors will affect the throughput of my VPN connection?
ANS: – VPN connection throughput depends on multiple factors, like the capacity of your customer gateway, the power of your network, average packet size, the protocol used, UDP vs. TCP, and the latency between your virtual private gateway and customer gateway.

WRITTEN BY Mayank Bharawa


 Login
Login


 March 6, 2023
March 6, 2023 PREV
PREV









Comments