|
Voiced by Amazon Polly |
Introduction
In today’s interconnected world, businesses often leverage multiple cloud providers to meet their diverse infrastructure needs. Amazon Web Services (AWS) and Google Cloud Platform (GCP) are two of the most prominent cloud providers, each offering various services and resources. Organizations frequently deploy a Site-to-Site VPN (Virtual Private Network) connection to create a seamless and secure network environment across these platforms. This comprehensive guide will walk you through the steps required to establish a Site-to-Site VPN connection between AWS and GCP.
Pioneers in Cloud Consulting & Migration Services
- Reduced infrastructural costs
- Accelerated application deployment
Importance of Site-to-Site VPN connection
- Seamless Data Transfer: Setting up a Site-to-Site VPN connection between GCP and AWS is crucial for businesses with dispersed data and applications across various cloud providers or on-premises centers. This VPN ensures secure and rapid data transfer, preventing slow and unreliable data movement that can disrupt operations and user satisfaction. Whether it’s data replication, database synchronization, or hybrid workloads, this connection guarantees seamless data flow, preserving data consistency and integrity between GCP and AWS.
- Enhanced Security: In today’s digital landscape, security is paramount, especially when managing multiple cloud environments like GCP and AWS. These providers have unique security measures and policies, challenging consistent security. Setting up a Site-to-Site VPN establishes a private, encrypted tunnel between the clouds, ensuring secure data transmission and protecting against internet threats. Additionally, access controls and firewall rules can be enforced to bolster security.
- High Availability and Redundancy: Business continuity is a crucial concern for all organizations, and cloud providers like GCP and AWS provide high availability options. However, creating redundancy across diverse cloud platforms demands careful preparation. Configuring a Site-to-Site VPN between GCP and AWS with redundancy in mind involves establishing multiple VPN tunnels along varied paths. This strategy guarantees continuous connectivity, even during network disruptions or maintenance, significantly lowering the chances of downtime and data loss.
- Cost Optimization: Cost optimization is vital in cloud management. A Site-to-Site VPN between GCP and AWS provides flexibility to select resources based on cost and performance, enabling efficient cloud spending. You can, for instance, opt for data processing in GCP and storage-intensive applications in AWS to maximize value from both providers while managing expenses effectively.
- Compliance and Governance: Adhering to industry-specific and regional compliance mandates across various cloud platforms is intricate. A Site-to-Site VPN ensures uniform network architecture and security measures in GCP and AWS, simplifying compliance management. This enables the application of consistent policies and controls in both environments and streamlines compliance reporting through centralized network traffic monitoring and auditing.
Steps to Set up a Site-to-Site VPN connection between AWS and GCP
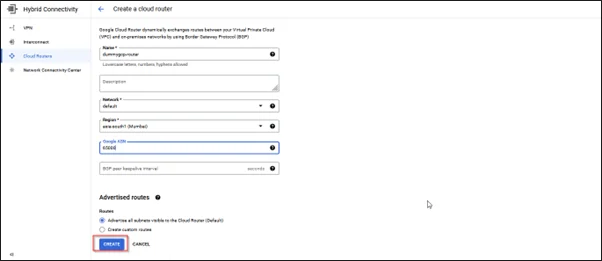
Step 1: Create Cloud Routers
- Sign in to the GCP Console
- Search for Hybrid connectivity and click on it
- In the HA connectivity on the left blade, select Cloud Routers
Step 2: Create a VPN in GCP
- Click on VPN on the left blade and Create a VPN

- Create a HA VPN

- Copy the 2 IPs listed in the interfaces.

Step 3: Create a Customer Gateway
In the AWS console:
- Navigate to the Amazon VPC dashboard.
- Click on ‘Customer Gateways’.
- As illustrated below, create customer gateways and input the copied IP address from the GCP tunnel interface into the designated IP address field.
- Create another Customer gateway for 2nd IP and repeat the same step as above.


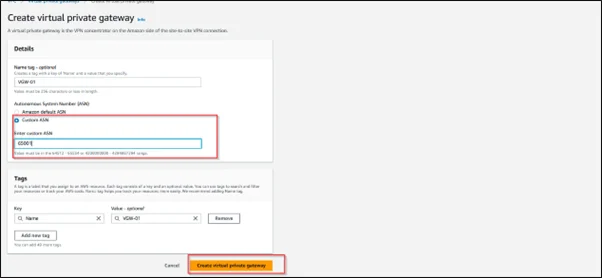
Step 4: Create a Virtual Private Gateway (AWS)
- Navigate to the Amazon VPC dashboard.
- Click on ‘Virtual Private Gateways’.
- Click on ‘Create Virtual Private Gateway’ and follow the prompts.
- Attach the Virtual Private Gateway to your Amazon VPC.

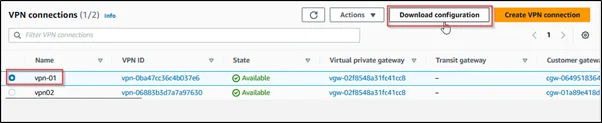
Step 5: Create an Amazon VPN Connection
- Navigate to the Amazon VPC dashboard.
- Select ‘Site-to-Site VPN connection’ and Click ‘Create VPN connection’.
- Choose the existing virtual private gateway in the ‘Target Gateway Type’ section. Then, from the drop-down menu for ‘Customer Gateway’, select one of the previously created customer gateways (CS01)
- Establish an additional VPN connection by including a second customer gateway (CS02) to ensure the high availability of the VPN.


- Select one of the VPNs in the VPN connection and click on ‘Download configuration.’
- In the Download configuration pop up, select the generic for the manufacturer of the customer gateway device.

- Repeat steps 6 and 7 for another VPN connection.
Step 6: Create Peer VPN Gateway
- Search for Hybrid connectivity VPN in the GCP console, click the Peer VPN Gateways, and create a new Peer VPN Gateway.
- Select four interfaces for the peer VPN gateway interface.


- From the download configuration, In the IPsec tunnel 1, copy the IP address from Virtual Private Gateway and paste it in the ‘interface 0 IP address’ dropdown.
- In the same download configuration inside IPsec tunnel 2, copy the IP address from Virtual Private Gateway and paste it into the ‘interface 1 IP address’ dropdown.
- Repeat the following steps inside another download configuration, copy the other virtual private gateway IPs, and paste them in the ‘interface 2 IP address’ dropdown and ‘interface 3 IP address’ dropdown.





Step 7: Add VPN Tunnel
- Navigate to the “Cloud VPN Gateways” section and select “Add VPN Tunnel.”

- Inside Add VPN Tunnel, select the drop downs as selected in the image below.

- We need to configure 4 VPN tunnels in the VPN tunnels and verify the VPN gateway interface and Associated peer VPN gateway interface.


- Add all the IKE pre-shared keys by repeating the same steps for the other 3 tunnels.
- After adding IKE pre-shared keys to all the VPN tunnels, click ‘create and continue’.

- Click on configure BGP session for all the VPN tunnels created
- Inside the Edit BGP session, add the peer ASN as 65001
- From the download configuration, Copy the inside IP address (AWS) of the customer gateway and virtual private gateway and paste it into the BGP IPv4 address dropdown inside the BGP session
- Repeat the similar steps and fill in the BGP IPv4 address from the download configuration




- VPN setup has been completed
- Check the status of the AWS VPN connection. The status of the VPN will be up.

- Edit route propagation in route table ‘yes’

Testing
- Create an Amazon EC2 instance in AWS and use the VPC to which we have attached a Virtual private gateway.
- Similarly, create the VM in the GCP, choose the default VPC, and attach a private IP to it.
- RDP into the Amazon EC2 instance and ping the private IP of the Google instance



Conclusion
This interconnected environment will enable seamless communication and data transfer between your cloud resources, fostering the agility and scalability needed to thrive in today’s competitive business landscape.
Drop a query if you have any questions regarding Site-to-Site VPN connection between AWS and GCP and we will get back to you quickly.
Making IT Networks Enterprise-ready – Cloud Management Services
- Accelerated cloud migration
- End-to-end view of the cloud environment
About CloudThat
CloudThat is an official AWS (Amazon Web Services) Advanced Consulting Partner and Training partner, AWS Migration Partner, AWS Data and Analytics Partner, AWS DevOps Competency Partner, Amazon QuickSight Service Delivery Partner, AWS EKS Service Delivery Partner, and Microsoft Gold Partner, helping people develop knowledge of the cloud and help their businesses aim for higher goals using best-in-industry cloud computing practices and expertise. We are on a mission to build a robust cloud computing ecosystem by disseminating knowledge on technological intricacies within the cloud space. Our blogs, webinars, case studies, and white papers enable all the stakeholders in the cloud computing sphere.
To get started, go through our Consultancy page and Managed Services Package, CloudThat’s offerings.
FAQs
1. Can I use Third-Party VPN appliances instead of Cloud Provider VPN Gateways?
ANS: – Yes, many organizations use third-party VPN appliances for their Site-to-Site VPNs. However, it requires additional configuration and compatibility checks.
2. Are there any bandwidth or data transfer limits for VPN connections?
ANS: – Yes, both AWS and GCP impose bandwidth and data transfer limits on VPN connections. These limits depend on your specific subscription or service tier.

WRITTEN BY H S Yashas Gowda
Yashas Gowda works as a Research Associate at CloudThat. He has good hands-on experience working on Azure and AWS services. He is interested to learn new technologies and tries to implement them.


 Login
Login


 September 20, 2023
September 20, 2023 PREV
PREV









Comments