Overview
Migrating Amazon Elastic Compute Cloud (EC2) instances across AWS accounts while ensuring data security is a critical task for many organizations. Whether you’re consolidating multiple accounts, moving workloads to a different AWS environment, or transferring instances to a partner or subsidiary, proper planning and execution are essential. In this blog, we will explore how to perform a secure and successful cross-account encrypted Amazon EC2 migration.
Pioneers in Cloud Consulting & Migration Services
- Reduced infrastructural costs
- Accelerated application deployment
Introduction
Cross-Account Encrypted EC2 Migration is a sophisticated and secure approach that allows organizations to seamlessly transfer EC2 instances from one AWS account to another while maintaining data confidentiality through encryption.
There are two types of AWS KMS keys.
- AMK (Amazon Managed Key): It is created, managed, owned by AWS, and used by AWS service integrated with AWS KMS.
- CMK (Customer Managed Key): It is created and managed by the user according to requirements and is owned by the user.
Pre-requisites
Before sharing your encrypted AMI and launch instances, you must set your AWS KMS key policy and AWS Identity and Access Management (IAM) policy.
This Demonstration requires two AWS accounts:
1. A source account to create a custom AMI and encrypt its Amazon EBS snapshots.
2. Target account launching instances with shared custom AMI with encrypted Snapshots.
Encryption Considerations
Decide whether to use the same AWS KMS key for encryption in both the source and destination accounts or create an AWS KMS key in the destination account and grant permissions for cross-account access.
Step-by-Step Migration Guide
- Create a CMK key in the source account
Go to the AWS console -> Search for AWS KMS -> Create customer managed key (CMK) that will be used to encrypt the AMI.

2. Share CMK key access to another account
Inside the CMK key, you will find the option to give access to other AWS accounts in the key policy tab.

Note: If you have an encrypted disk via CMK, skip Step 3.
3. Create a new volume to change the encryption key
From the Snapshot of the encrypted Amazon EC2 instance, create a new volume for changing the encryption from AMK to CMK.
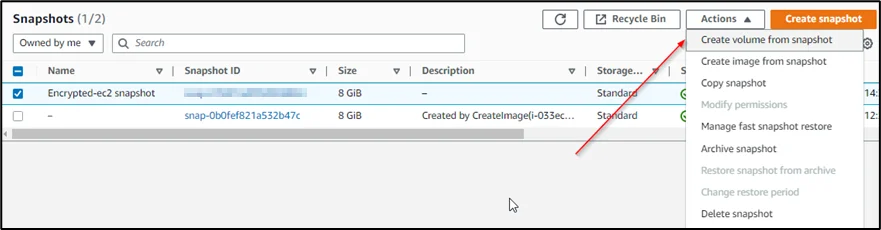
While creating the volume from the snapshot you will find AWS KMS key option to select the KMS key. Select the CMK key that you have created in Step 1.

You will find that the encryption key has changed to the CMK key. So that you can now create a snapshot and share it with another account

4. Create a Snapshot of the new volume
Create a snapshot from the new volume created with the CMK key.

5. Create AMI from a New snapshot
Create an image and note down the AMI-id to be required later on.

6. Create the policy setting for the source account
In the below policy change, the AMI ID that has been noted from the previous step
Policy:
7. Create the policy setting for the target account
8. Give AMI permission to the Destination Account


9. Find the shared AMI in the destination account, and now you can use that image to launch a new instance

Conclusion
Cross-account encrypted Amazon EC2 migration is a complex but necessary process for organizations that need to restructure their AWS resources for various reasons, including compliance, security, and cost management. Following the steps outlined in this blog and carefully planning the migration, you can ensure a smooth and secure transition of your Amazon EC2 instances to a new AWS account while maintaining data integrity and security. Documentation and testing are essential throughout the migration process to mitigate potential issues and minimize downtime. With the right strategy and attention to detail, you can successfully navigate the challenges of cross-account Amazon EC2 migration and achieve your organization’s goals.
Drop a query if you have any questions regarding Cross-account encrypted Amazon EC2 Migration and we will get back to you quickly.
Making IT Networks Enterprise-ready – Cloud Management Services
- Accelerated cloud migration
- End-to-end view of the cloud environment
About CloudThat
CloudThat is an official AWS (Amazon Web Services) Advanced Consulting Partner and Training partner, AWS Migration Partner, AWS Data and Analytics Partner, AWS DevOps Competency Partner, Amazon QuickSight Service Delivery Partner, AWS EKS Service Delivery Partner, and Microsoft Gold Partner, helping people develop knowledge of the cloud and help their businesses aim for higher goals using best-in-industry cloud computing practices and expertise. We are on a mission to build a robust cloud computing ecosystem by disseminating knowledge on technological intricacies within the cloud space. Our blogs, webinars, case studies, and white papers enable all the stakeholders in the cloud computing sphere.
To get started, go through our Consultancy page and Managed Services Package, CloudThat’s offerings.
FAQs
1. What is the difference between the AMK and CMK keys?
ANS: – AMK key is created, managed, owned by AWS, and used by AWS service integrated with AWS KMS. CMK key is created, managed by the user according to requirements, and owned by the user.
2. How can I ensure minimal downtime during migration?
ANS: – To minimize downtime, plan the migration during periods of lower traffic. Additionally, consider using AWS Elastic Load Balancers or other failover mechanisms to route traffic to the new instances seamlessly.

WRITTEN BY Kashyap Nitinbhai Shani
Kashyap Nitinbhai Shani is a Research Associate at CloudThat. He is interested to learn advanced technologies and gain insights into new and upcoming cloud services. He likes writing tech blogs and learning new languages.


 Login
Login


 September 20, 2023
September 20, 2023 PREV
PREV









Comments